York research collaboration to improve cybersecurity threat detection, mitigation

York research collaboration to improve cybersecurity threat detection, mitigation
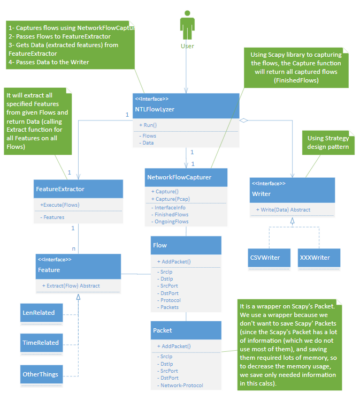
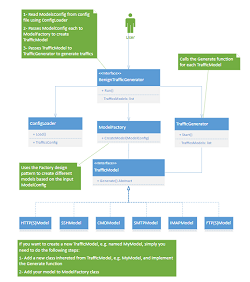
Advancing Leadership in Cybersecurity York University’s Behaviour-Centric Cybersecurity Center (BCCC) is advancing leadership in cybersecurity by collaborating with cPacket – a network monitoring company – to tackle a major cybercrime threat. Join us on a journey of navigating the intricate landscape of cybersecurity, where empowerment takes center A significant challenge in cybercrime is a distributed […]