At York University’s Behaviour-Centric Cybersecurity Center (BCCC), we are advancing research and innovation in securing next-generation digital infrastructure by focusing on real-world challenges across IoT, OT, IIoT, DeFi systems, smart contracts, healthcare technologies, and beyond. As a leading center in Cyber Threat Intelligence (CTI), BCCC develops and operationalizes intelligence-driven approaches to proactively detect, analyze, and mitigate emerging cyber threats. The rapid evolution of Industry 4.0 has led to a convergence of information technologies (IT) and operational technologies (OT), introducing complex cybersecurity challenges, from zero-day vulnerabilities in smart medical devices to sophisticated attacks on decentralized financial ecosystems and industrial automation systems.
BCCC has developed a series of specialized testbeds using CFI and ORF funding to address the growing need for adaptive and high-quality cybersecurity datasets. These environments replicate real-world conditions across critical domains while maintaining privacy and control. Our current infrastructure includes four active testbeds: (1) a Honeynet environment for malware behavior simulation and threat intelligence gathering; (2) an IoT transportation testbed supporting Connected and Autonomous Vehicle (CAV) network security; (3) a Smart City IoT/IIoT platform targeting threat analysis in public infrastructure, energy systems, and industrial automation; and (4) a Threat Hunting platform for AI-based malware analysis and intrusion detection in hybrid environments.
In addition, BCCC is pioneering research in DeFi security and smart contract vulnerabilities by modeling transaction behaviors and detecting anomalies in blockchain-based platforms. Our healthcare security efforts focus on protecting wearable and remote monitoring devices, using AI to detect protocol-specific threats in Bluetooth, Zigbee, Z-Wave, and Wi-Fi communications. Through these diverse, multidisciplinary projects, we generate large-scale behavioral datasets and AI-powered detection models to improve cybersecurity resilience across interconnected sectors.
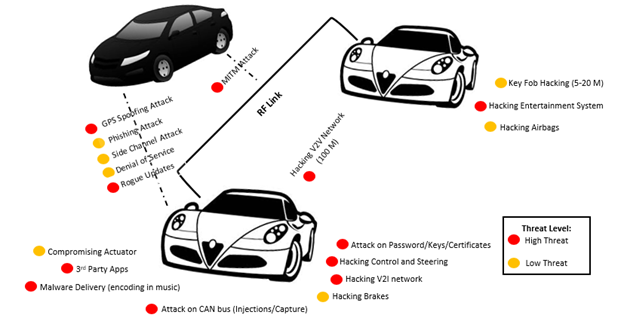
Transportation Network Security
The rise of connected and automated vehicles (CAVs) presents transformative opportunities for the automobile industry, yet certain obstacles must be overcome before widespread deployment is viable. Incorporating smart devices and communications into CAVs introduces critical cybersecurity risks and safety considerations. Unfortunately, these systems' interconnected nature and automation render them more susceptible to cyberattacks, including in-vehicle attacks and communication breaches. Consequently, new cybersecurity risks emerge. However, connectedness and automation make these systems more vulnerable and increase the consequences of cyberattacks, including in-vehicle attacks (e.g., hijacking attacks) and vehicle-to-everything communication attacks (e.g., data theft), introducing new cybersecurity risks. The consequences of a CAV being hacked could result in compromised features, resulting in accidents, damage, financial loss, personal injury, and even death. The objective of this R&D project is to design, develop, and implement an intelligence-driven solution as a holistic countermeasure and evaluate the final solution in our CAV test-bed, including more than 32 transportation network IIoT devices.
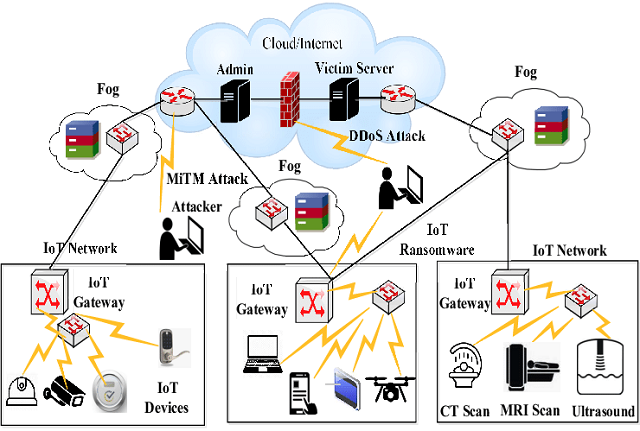
IoT and IIoT Network Security
Recently, the increasing popularity of the Internet of Things (IoT) has opened up promising opportunities for advancing home automation systems and various industrial applications. This has led to the emergence of the Industrial Internet of Things (IIoT), bringing automation to industries. However, with these advancements, IoT faces numerous cybersecurity challenges requiring innovative approaches to ensure robust security. Furthermore, the security vulnerabilities associated with IIoT are even more concerning. This R&D project aims to address these challenges by extensively researching cybersecurity threats and their management within IoT and IIoT network traffic. The insights gained from this research will be utilized to propose, design, and develop several intelligence-driven solutions that serve as a comprehensive countermeasure to mitigate these threats effectively. We will text and evaluate the final solutions in our IoI-IIoT testbeds, including over 75 Internet of Things devices and equipment.

Universal Anomaly Profile (UAP)
Anomaly detection aims to find data activity patterns that do not conform to established and expected behaviours. Anomaly detection has many applications, such as detecting intrusion, fraud, data leakage, etc. The main idea in this project is to build a typical hierarchical profile for an organization’s benign users, called a Universal User Profile (UUP), and a profile for users with behavioral anomalies, or “bad users”, a Universal Anomaly Profile (UAP). The proposed model will be called Universal Anomaly Detection (UAD) and, along with a human-centric infographic model, will contain multiple data visualization techniques to allow for improved visibility, faster troubleshooting, and streamlined onboarding. It will be developed as a new component for all available IT systems security management solutions, including Intrusion Detection and Prevention Systems (IDS/IPS), Unified Threat Management (UTM), Security Information and Event Management (SIEM), etc.. It will be tested using our network security testbed, including 50 VMs (covering different OSs and user behaviours) and 11 servers (such as Web Server, email server, Database Server, DNS Server, File server, FTP server, DHCP server, etc.).

Smart Contracts Vulnerabilities Profiling
Smart Contracts are self-executing programs operating on blockchains like Ethereum, with a significant role in decentralized applications and cryptocurrency management. However, they are susceptible to attacks due to technical flaws in design and implementation. Smart Contracts enable automated and trustless agreements without intermediaries, and their immutability after deployment on the blockchain makes security considerations crucial during development. Nonetheless, recent devastating attacks and numerous vulnerabilities have raised concerns about the technology's sustainability. While Smart Contracts offer a powerful tool for developing decentralized applications, their implementation on blockchain platforms introduces security challenges stemming from programming vulnerabilities, which can lead to substantial economic consequences. This project aims to create a Universal vulnerability profiling system for Smart Contracts to address these issues.

Decentralized Finance Security (DeFi Sec)
This project focuses on enhancing security in Decentralized Finance (DeFi) by addressing the unique challenges of fraudulent activities in a decentralized ecosystem. Unlike Centralized Finance (CeFi), which relies on advanced fraud detection systems incorporating AI-powered models, DeFi introduces vulnerabilities due to its pseudo-anonymous nature, smart contract flaws, and lack of regulatory oversight. These factors create new opportunities for malicious actors, necessitating innovative detection and prevention methods. The project aims to develop and implement cutting-edge solutions tailored to the DeFi landscape, ensuring robust security, safeguarding user assets, and mitigating risks associated with decentralized financial operations.
Partners and Collaborators:








Research Funding and Institutional Support
We acknowledge the support of the Canada Foundation for Innovation (CFI) (JELF and IoF) and the Ontario Research Fund (ORF) for the infrastructure funds.